¶ SSL 协议配置参考
¶ SSL 证书配置
若站点需要开放 HTTPS 访问,只需在配置站点时为对应的端口启用 SSL 配置即可(需要上传 SSL 证书)。
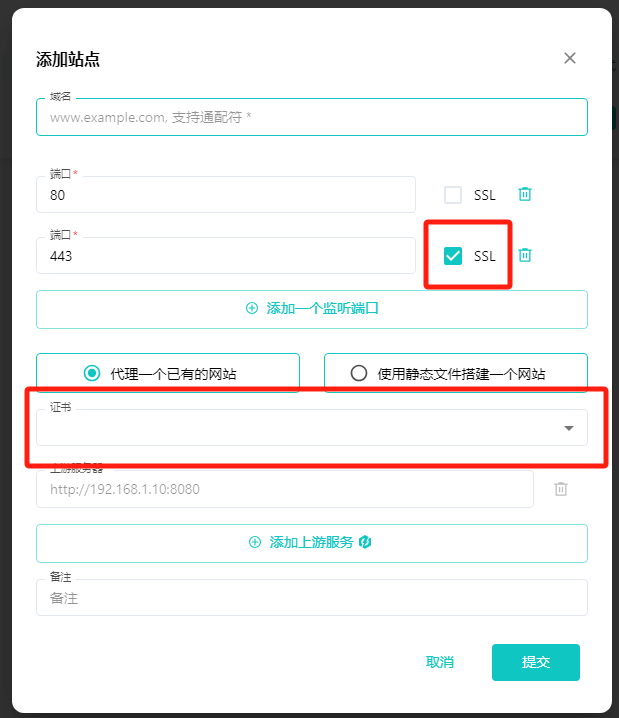
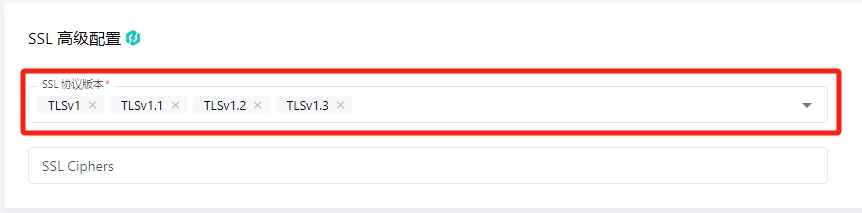
¶ SSL 协议版本配置
如需修改 HTTPS 协议的 SSL 版本,可在 SSL 高级配置 中进行选择。
雷池当前支持:TLSv1、TLSv1.1、TLSv1.2、TLSv1.3、SSLv2、SSLv3
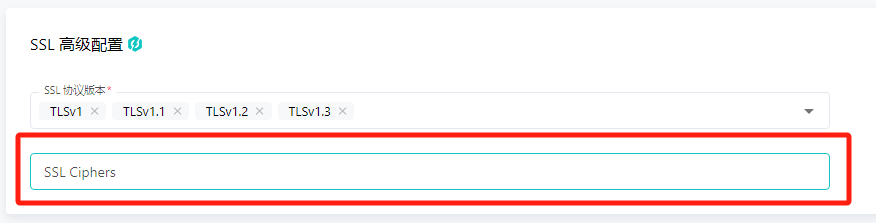
¶ SSL 密码算法配置
在某些场景下,Web 业务可能会对 SSL 加密算法的安全强度有所要求,或是某些加密算法被爆出了安全漏洞,这种情况下需要修改 SSL 的加密算法才能让问题得到缓解。
雷池提供 SSL 加密 Cipher 的自定义功能,见 SSL 高级配置
¶ 一些常见的 SSL Cipher 组合
- Nginx 官方实例:
AES128-SHA:AES256-SHA:RC4-SHA:DES-CBC3-SHA:RC4-MD5; - Cloudflare 推荐:
[ECDHE-ECDSA-AES128-GCM-SHA256|ECDHE-ECDSA-CHACHA20-POLY1305|ECDHE-RSA-AES128-GCM-SHA256|ECDHE-RSA-CHACHA20-POLY1305]:ECDHE+AES128:RSA+AES128:ECDHE+AES256:RSA+AES256:ECDHE+3DES:RSA+3DES - Mozilla 推荐(Modern compatibility TLS 1.3):
TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 - Mozilla 推荐(Intermediate compatibility TLS 1.3):
TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 - Mozilla 推荐(Intermediate compatibility TLS 1.2):
ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305 - [Mozilla 推荐(Old backward compatibility TLS 1.0 - 1.2)]:
ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA256:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA - Mozilla 推荐:
ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305; - Cipherli 推荐:
EECDH+AESGCM:EDH+AESGCM - 高强度加密套件:
HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4:!RSA;